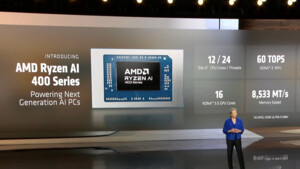
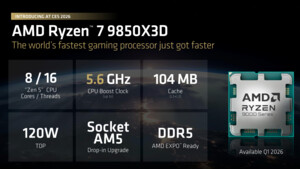
so habs mal mit dem WinDbg hinbekommen,
hab die letzten 2 screens geladen vllt könnt ihr das ja lesen

dem ram test werde ich auch gleich mal durchführen.
Loading Dump File [C:\Windows\Minidump\Mini011310-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:Symbolsr*
http://msdl.microsoft.com/download/symbols;SRV*Neuer Ordner*
http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows Server 2008/Windows Vista Kernel Version 6001 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 6001.18304.amd64fre.vistasp1_gdr.090805-0102
Machine Name:
Kernel base = 0xfffff800`01c52000 PsLoadedModuleList = 0xfffff800`01e17db0
Debug session time: Wed Jan 13 00:08:53.361 2010 (GMT+1)
System Uptime: 0 days 0:03:49.489
Loading Kernel Symbols
...............................................................
................................................................
..
Loading User Symbols
Loading unloaded module list
.....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 50, {fffff8a009dffb00, 1, fffff80001d868bf, 5}
Could not read faulting driver name
Probably caused by : Pool_Corruption ( nt!ExDeferredFreePool+1bf )
Followup: Pool_corruption
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
PAGE_FAULT_IN_NONPAGED_AREA (50)
Invalid system memory was referenced. This cannot be protected by try-except,
it must be protected by a Probe. Typically the address is just plain bad or it
is pointing at freed memory.
Arguments:
Arg1: fffff8a009dffb00, memory referenced.
Arg2: 0000000000000001, value 0 = read operation, 1 = write operation.
Arg3: fffff80001d868bf, If non-zero, the instruction address which referenced the bad memory
address.
Arg4: 0000000000000005, (reserved)
Debugging Details:
------------------
Could not read faulting driver name
WRITE_ADDRESS: GetPointerFromAddress: unable to read from fffff80001e7b080
fffff8a009dffb00
FAULTING_IP:
nt!ExDeferredFreePool+1bf
fffff800`01d868bf 488908 mov qword ptr [rax],rcx
MM_INTERNAL_CODE: 5
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x50
PROCESS_NAME: svchost.exe
CURRENT_IRQL: 0
TRAP_FRAME: fffffa600a2a5810 -- (.trap 0xfffffa600a2a5810)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffff8a009dffb00 rbx=0000000000000000 rcx=fffff88009929580
rdx=fffff88009ef0410 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80001d868bf rsp=fffffa600a2a59a0 rbp=0000000000000000
r8=fffff88009ef0000 r9=fffff88009eed740 r10=0000000000000001
r11=0000000000000001 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na pe nc
nt!ExDeferredFreePool+0x1bf:
fffff800`01d868bf 488908 mov qword ptr [rax],rcx ds:5960:fffff8a0`09dffb00=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80001cb47e2 to fffff80001ca66d0
STACK_TEXT:
fffffa60`0a2a5718 fffff800`01cb47e2 : 00000000`00000050 fffff8a0`09dffb00 00000000`00000001 fffffa60`0a2a5810 : nt!KeBugCheckEx
fffffa60`0a2a5720 fffff800`01ca5259 : 00000000`00000001 00000000`000013e0 fffffa80`081e9b00 fffff880`0a026010 : nt!MmAccessFault+0x4f2
fffffa60`0a2a5810 fffff800`01d868bf : fffffa80`0870b7f0 00000000`00000017 fffffa80`05e09e60 fffff800`01d855fc : nt!KiPageFault+0x119
fffffa60`0a2a59a0 fffff800`01d85f6a : fffff880`0a110cf0 00000000`00000000 00000000`00000001 00000000`00000000 : nt!ExDeferredFreePool+0x1bf
fffffa60`0a2a5a10 fffffa60`00a9d963 : fffffa80`044fb520 fffffa80`0870b7f0 fffff780`00000001 00000000`6e664d46 : nt!ExFreePoolWithTag+0x3aa
fffffa60`0a2a5ac0 fffffa60`00a7bda7 : fffffa80`043cc490 fffffa80`0870b7f0 fffffa80`044fb590 00000000`00000000 : fltmgr! ?? ::NNGAKEGL::`string'+0x1b82
fffffa60`0a2a5af0 fffffa60`00a87094 : 00000000`00008000 fffffa80`044fb520 00000000`00000000 fffffa80`044fb590 : fltmgr!FltpGetFileNameInformation+0x277
fffffa60`0a2a5b90 fffffa60`00ac630f : fffffa80`0870b7f0 fffff880`0a1096f0 00000000`00000000 fffffa60`0a2a5cc0 : fltmgr!FltGetFileNameInformation+0x174
fffffa60`0a2a5c20 fffffa60`00ac4c16 : 00000000`00000000 fffff800`00000001 00000000`00000000 00000000`00002ecc : fileinfo!FIStreamGetInfo+0x11f
fffffa60`0a2a5ca0 fffffa60`00a7af0c : fffffa80`044f3fb0 fffffa60`0a2a5d68 fffff880`0a1096f0 00000000`00000000 : fileinfo!FIPostCreateCallback+0x17a
fffffa60`0a2a5d20 fffffa60`00a78f5d : fffffa80`04c73030 fffffa80`044b7980 fffffa80`07425010 fffffa80`07425230 : fltmgr!FltpPerformPostCallbacks+0x31d
fffffa60`0a2a5df0 fffffa60`00a9526c : fffffa80`0490f8e0 fffffa80`05e098d0 fffffa80`044f3c00 fffffa60`0a2a5eb0 : fltmgr!FltpLegacyProcessingAfterPreCallbacksCompleted+0x36d
fffffa60`0a2a5e60 fffff800`01f2cf13 : 00000000`00000060 00000000`00000240 fffffa80`04023568 fffff880`006e2b90 : fltmgr!FltpCreate+0x25d
fffffa60`0a2a5f10 fffff800`01f26802 : fffffa80`0490f8e0 00000000`00000000 fffffa80`040c9b10 fffffa60`0101fc00 : nt!IopParseDevice+0x5e3
fffffa60`0a2a60b0 fffff800`01f2aad4 : ffffffff`80001494 fffffa80`086e7d00 00000000`00000240 00000000`00000000 : nt!ObpLookupObjectName+0x202
fffffa60`0a2a61c0 fffff800`01f37080 : fffffa80`00100001 fffffa60`0a2a6670 00000000`00000000 fffffa80`039c1580 : nt!ObOpenObjectByName+0x2f4
fffffa60`0a2a6290 fffff800`01f037da : fffffa60`0a2a6558 00000000`00100001 fffff880`006e2b90 fffffa60`0a2a6590 : nt!IopCreateFile+0x290
fffffa60`0a2a6330 fffffa60`00a96dc9 : 00000000`00000000 fffffa60`0a2a6660 00000000`00000000 00000000`00100001 : nt!IoCreateFileEx+0xfa
fffffa60`0a2a63d0 fffffa60`00ac7f50 : 00000000`00000007 00000000`00000000 fffffa60`0a2a6558 fffffa60`0a2a6548 : fltmgr!FltCreateFileEx2+0x169
fffffa60`0a2a64c0 fffff800`01fabf67 : fffffa80`039fa301 00000000`00000001 fffff880`0a1044f0 fffffa80`05d76d60 : fileinfo!FIPfInterfaceOpen+0x400
fffffa60`0a2a6640 fffff800`0204c769 : fffff880`09e6a5d0 ffffffff`ffe91ca0 fffffa60`0a2a6828 00000000`00000000 : nt!PfpOpenHandleCreate+0x117
fffffa60`0a2a6710 fffff800`0204d5d5 : 00000000`00000002 00000000`000090f0 fffff880`09f28198 00000000`00000305 : nt!PfpPrefetchDirectoryStream+0xb9
fffffa60`0a2a67c0 fffff800`0208049e : fffff880`00000002 00000000`00000000 00000000`00004021 00000000`00000000 : nt!PfpVolumePrefetchMetadata+0x3d5
fffffa60`0a2a68c0 fffff800`02080782 : 00000000`00000000 fffffa60`0a2a6ca0 fffffa60`0a2a6a08 fffff880`09f1f001 : nt!PfpPrefetchRequestPerform+0x2ce
fffffa60`0a2a6960 fffff800`020809e6 : fffffa60`0a2a6a08 00000000`00000001 fffffa80`089e8f20 00000000`00000000 : nt!PfpPrefetchRequest+0x171
fffffa60`0a2a69d0 fffff800`02093118 : 00000000`00000000 00000000`00000004 fffffa80`03d41000 00000000`00000001 : nt!PfSetSuperfetchInformation+0x1a5
fffffa60`0a2a6ab0 fffff800`01ca6173 : fffffa80`08cfebb0 00000000`00000000 00000000`00000000 fffffa80`089e70e0 : nt!NtSetSystemInformation+0x8fb
fffffa60`0a2a6c20 00000000`777470ea : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`04baf7c8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x777470ea
STACK_COMMAND: kb
FOLLOWUP_IP:
nt!ExDeferredFreePool+1bf
fffff800`01d868bf 488908 mov qword ptr [rax],rcx
SYMBOL_STACK_INDEX: 3
SYMBOL_NAME: nt!ExDeferredFreePool+1bf
FOLLOWUP_NAME: Pool_corruption
IMAGE_NAME: Pool_Corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
MODULE_NAME: Pool_Corruption
FAILURE_BUCKET_ID: X64_0x50_nt!ExDeferredFreePool+1bf
BUCKET_ID: X64_0x50_nt!ExDeferredFreePool+1bf
Followup: Pool_corruption
---------
NUMMER 2:
Microsoft (R) Windows Debugger Version 6.11.0001.404 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\Mini011310-02.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:Symbolsr*
http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows Server 2008/Windows Vista Kernel Version 6001 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 6001.18304.amd64fre.vistasp1_gdr.090805-0102
Machine Name:
Kernel base = 0xfffff800`01c13000 PsLoadedModuleList = 0xfffff800`01dd8db0
Debug session time: Wed Jan 13 11:08:53.401 2010 (GMT+1)
System Uptime: 0 days 0:02:17.153
Loading Kernel Symbols
...............................................................
................................................................
..
Loading User Symbols
Loading unloaded module list
....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 19, {21, fffff900c0182000, 3550, 0}
Probably caused by : win32k.sys ( win32k!EngFreeMem+21 )
Followup: MachineOwner
---------
3: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
BAD_POOL_HEADER (19)
The pool is already corrupt at the time of the current request.
This may or may not be due to the caller.
The internal pool links must be walked to figure out a possible cause of
the problem, and then special pool applied to the suspect tags or the driver
verifier to a suspect driver.
Arguments:
Arg1: 0000000000000021, the data following the pool block being freed is corrupt. Typically this means the consumer (call stack ) has overrun the block.
Arg2: fffff900c0182000, The pool pointer being freed.
Arg3: 0000000000003550, The number of bytes allocated for the pool block.
Arg4: 0000000000000000, The corrupted value found following the pool block.
Debugging Details:
------------------
BUGCHECK_STR: 0x19_21
POOL_ADDRESS: GetPointerFromAddress: unable to read from fffff80001e3c080
fffff900c0182000
CUSTOMER_CRASH_COUNT: 2
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
PROCESS_NAME: csrss.exe
CURRENT_IRQL: 0
LAST_CONTROL_TRANSFER: from fffff80001d47e2b to fffff80001c676d0
STACK_TEXT:
fffffa60`08442f38 fffff800`01d47e2b : 00000000`00000019 00000000`00000021 fffff900`c0182000 00000000`00003550 : nt!KeBugCheckEx
fffffa60`08442f40 fffff960`001591f1 : fffffa60`084430a0 00000000`00000000 00000000`00000021 fffffa60`64667454 : nt!ExDeferredFreePool+0x775
fffffa60`08442ff0 fffff960`0015b04a : 00000000`01d7a4a0 fffffa60`084430a0 00000000`000005f4 00000000`01d725f0 : win32k!EngFreeMem+0x21
fffffa60`08443020 fffff960`00108523 : fffff900`c00e4760 00000000`00000001 00000000`00000001 00000000`00000000 : win32k!bLoadGlyphSet+0x162
fffffa60`08443050 fffff960`001081c6 : fffff900`c00e4760 fffff900`00000001 fffff900`c00e4760 fffff960`0010809e : win32k!bReloadGlyphSet+0x267
fffffa60`08443710 fffff960`0010810c : 00000000`00000000 fffff900`c00e4760 fffffa60`00000001 00000000`00000001 : win32k!ttfdQueryFontTree+0x66
fffffa60`08443760 fffff960`00153d27 : fffff960`001080ac fffff900`c00e4b00 00000000`00000001 00000000`00000000 : win32k!ttfdSemQueryFontTree+0x60
fffffa60`084437a0 fffff960`00153be4 : fffffa60`08443850 fffffa60`08443880 00000000`00000000 fffffa60`08443a80 : win32k!PDEVOBJ::QueryFontTree+0x57
fffffa60`084437f0 fffff960`0014953e : fffff900`c000a010 fffff900`c1c5f954 fffffa60`084439e8 00000000`00000000 : win32k!PFEOBJ:

fdg+0x90
fffffa60`08443850 fffff960`0016b763 : fffff900`c1c5f840 fffffa60`08443ad0 fffffa60`084439d8 fffffa60`08443b20 : win32k!RFONTOBJ::bRealizeFont+0x46
fffffa60`08443970 fffff960`0014c091 : 00000000`10010000 fffff900`00000000 00000000`00000000 0035e564`00000002 : win32k!RFONTOBJ::bInit+0x523
fffffa60`08443a80 fffff960`0014c01f : 00000000`00000000 fffffa60`08443ca0 00000000`70616d63 00000000`240a03dc : win32k!ulGetFontData2+0x31
fffffa60`08443af0 fffff960`0014beed : 00000000`ffffffff 00000000`ffffffff fffff900`c00e6540 fffff900`c0001000 : win32k!ulGetFontData+0x7f
fffffa60`08443b40 fffff800`01c67173 : 00000000`230108f1 00000000`00000000 00000000`0012dda8 00000000`00000000 : win32k!NtGdiGetFontData+0x4d
fffffa60`08443bb0 00000000`7586ad3a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`0012dd88 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x7586ad3a
STACK_COMMAND: kb
FOLLOWUP_IP:
win32k!EngFreeMem+21
fffff960`001591f1 4883c420 add rsp,20h
SYMBOL_STACK_INDEX: 2
SYMBOL_NAME: win32k!EngFreeMem+21
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: win32k
IMAGE_NAME: win32k.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4a857827
FAILURE_BUCKET_ID: X64_0x19_21_win32k!EngFreeMem+21
BUCKET_ID: X64_0x19_21_win32k!EngFreeMem+21
Followup: MachineOwner
---------
3: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
BAD_POOL_HEADER (19)
The pool is already corrupt at the time of the current request.
This may or may not be due to the caller.
The internal pool links must be walked to figure out a possible cause of
the problem, and then special pool applied to the suspect tags or the driver
verifier to a suspect driver.
Arguments:
Arg1: 0000000000000021, the data following the pool block being freed is corrupt. Typically this means the consumer (call stack ) has overrun the block.
Arg2: fffff900c0182000, The pool pointer being freed.
Arg3: 0000000000003550, The number of bytes allocated for the pool block.
Arg4: 0000000000000000, The corrupted value found following the pool block.
Debugging Details:
------------------
BUGCHECK_STR: 0x19_21
POOL_ADDRESS: fffff900c0182000
CUSTOMER_CRASH_COUNT: 2
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
PROCESS_NAME: csrss.exe
CURRENT_IRQL: 0
LAST_CONTROL_TRANSFER: from fffff80001d47e2b to fffff80001c676d0
STACK_TEXT:
fffffa60`08442f38 fffff800`01d47e2b : 00000000`00000019 00000000`00000021 fffff900`c0182000 00000000`00003550 : nt!KeBugCheckEx
fffffa60`08442f40 fffff960`001591f1 : fffffa60`084430a0 00000000`00000000 00000000`00000021 fffffa60`64667454 : nt!ExDeferredFreePool+0x775
fffffa60`08442ff0 fffff960`0015b04a : 00000000`01d7a4a0 fffffa60`084430a0 00000000`000005f4 00000000`01d725f0 : win32k!EngFreeMem+0x21
fffffa60`08443020 fffff960`00108523 : fffff900`c00e4760 00000000`00000001 00000000`00000001 00000000`00000000 : win32k!bLoadGlyphSet+0x162
fffffa60`08443050 fffff960`001081c6 : fffff900`c00e4760 fffff900`00000001 fffff900`c00e4760 fffff960`0010809e : win32k!bReloadGlyphSet+0x267
fffffa60`08443710 fffff960`0010810c : 00000000`00000000 fffff900`c00e4760 fffffa60`00000001 00000000`00000001 : win32k!ttfdQueryFontTree+0x66
fffffa60`08443760 fffff960`00153d27 : fffff960`001080ac fffff900`c00e4b00 00000000`00000001 00000000`00000000 : win32k!ttfdSemQueryFontTree+0x60
fffffa60`084437a0 fffff960`00153be4 : fffffa60`08443850 fffffa60`08443880 00000000`00000000 fffffa60`08443a80 : win32k!PDEVOBJ::QueryFontTree+0x57
fffffa60`084437f0 fffff960`0014953e : fffff900`c000a010 fffff900`c1c5f954 fffffa60`084439e8 00000000`00000000 : win32k!PFEOBJ:

fdg+0x90
fffffa60`08443850 fffff960`0016b763 : fffff900`c1c5f840 fffffa60`08443ad0 fffffa60`084439d8 fffffa60`08443b20 : win32k!RFONTOBJ::bRealizeFont+0x46
fffffa60`08443970 fffff960`0014c091 : 00000000`10010000 fffff900`00000000 00000000`00000000 0035e564`00000002 : win32k!RFONTOBJ::bInit+0x523
fffffa60`08443a80 fffff960`0014c01f : 00000000`00000000 fffffa60`08443ca0 00000000`70616d63 00000000`240a03dc : win32k!ulGetFontData2+0x31
fffffa60`08443af0 fffff960`0014beed : 00000000`ffffffff 00000000`ffffffff fffff900`c00e6540 fffff900`c0001000 : win32k!ulGetFontData+0x7f
fffffa60`08443b40 fffff800`01c67173 : 00000000`230108f1 00000000`00000000 00000000`0012dda8 00000000`00000000 : win32k!NtGdiGetFontData+0x4d
fffffa60`08443bb0 00000000`7586ad3a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`0012dd88 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x7586ad3a
STACK_COMMAND: kb
FOLLOWUP_IP:
win32k!EngFreeMem+21
fffff960`001591f1 4883c420 add rsp,20h
SYMBOL_STACK_INDEX: 2
SYMBOL_NAME: win32k!EngFreeMem+21
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: win32k
IMAGE_NAME: win32k.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4a857827
FAILURE_BUCKET_ID: X64_0x19_21_win32k!EngFreeMem+21
BUCKET_ID: X64_0x19_21_win32k!EngFreeMem+21
Followup: MachineOwner